Updates from Enzoic’s Threat Research Team
Unquestionably, infostealers still take the top spot as the most prominent source for newly compromised credentials (and potentially other PII as well). Access brokers are buying, selling, trading, collecting, packaging, and distributing the raw logs and collections of the extracted stolen credentials at a rate of millions of lines per day. While much of this is certainly aggregated lists and repackaged collections, this high trading rate indicates the utility and popularity of this data among threat actors.
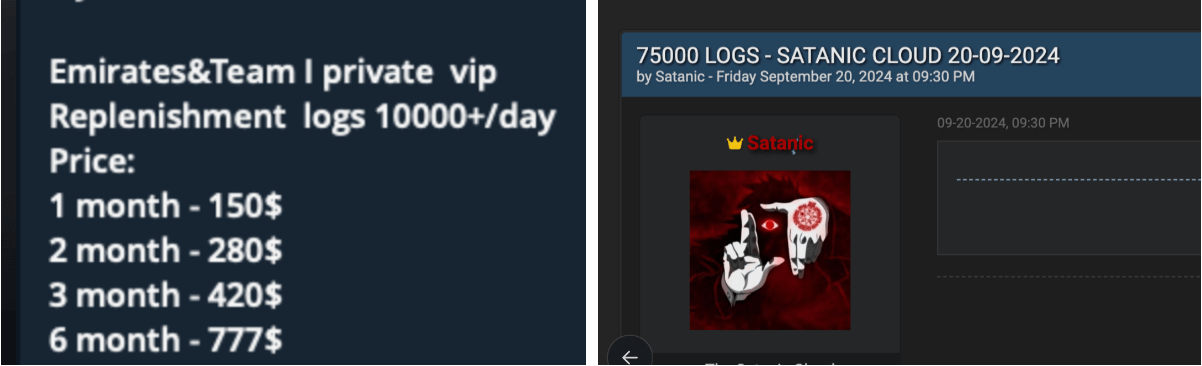 Various threat actors posting stealer logs for download or sale.
Various threat actors posting stealer logs for download or sale.
While infostealers and related traffic steal the show, organizational breaches continue to occur as well. Data from the UK seat-filling service Central Tickets was posted on Sept 20th, exposing business records, customer information, and authentication information (including hashed passwords). Some users reported difficulty accessing accounts and increases in phishing emails as a result of the breach.
Breach notification service HaveIBeenPwned also posted about the now-defunct site Gamesbox.com, which was determined to have been breached in 2020 and was found earlier this year in the large data dump known as the MOAB. Enzoic had already obtained and ingested this data several years ago.
Also concerning is the expanding capabilities of infostealers. Recent research by Recorded Future revealed that the Rhadamanthys infostealer has begun to leverage Optical Character Recognition (OCR), a type of computer vision that allows text in graphics to be converted to standard digitally encoded text. This means that any information found in images can be used more easily and automatically by hackers, and is being leveraged to steal cryptocurrency as detailed in the report.
We regularly observe large amounts of extremely sensitive PII being traded as images among threat actors, such as pictures of government ID documents like passports or Social Security cards, often along with pictures of the owner. Criminals can use these to perpetrate identity theft that can be absolutely devastating to victims, with years of consequences. With these types of OCR tools becoming more prevalent and easier for end-use fraudsters and access brokers to leverage, we should brace for higher levels than ever of identity theft as extraction of the information in these photographs becomes automated and highly available to cyber criminals.
 Photos like this, often used for ID verification by many agencies and services, are highly valuable to identity thieves and increasingly susceptible to exploitation.
Photos like this, often used for ID verification by many agencies and services, are highly valuable to identity thieves and increasingly susceptible to exploitation.
Four years ago, the last time the US was preparing for a presidential election, large cyber-forensics teams like those at Microsoft warned us that massive credential stuffing campaigns by large nation-state actors were taking place against campaign workers, election officials, and other political figures. With global unrest among many of these same nations extremely high at the moment and another contentious election approaching, users in these areas should take extra care to use strong passwords and monitor accounts for unusual activity.
1. What is infostealer malware and how does it lead to credential compromise?
Infostealers are a kind of malware-as-a-service (MaaS) that exfiltrate data from infected computers to a central server, which is then sold and published as “logs”- comprehensive profiles of the data from each compromised computer. The stolen data comes primarily from the ‘autofill’ and password managers in the user’s web browsers, but stealers also grab files from the Desktop and Documents folders, browser cookies, cryptocurrency wallets, and information from other services like VPNs, Discord, or Telegram if they are installed on the system. These stolen credentials and other data can then be sold or shared on the dark web, within hacker communities, or on known cybercrime communication platforms.
2. Why is compromised credential monitoring crucial for preventing account takeover?
Compromised credential monitoring involves scanning dark web marketplaces, cybercrime forums, threat actor communication platforms, and other sources for stolen credentials. With active, real-time monitoring, organizations can quickly identify if their credentials have been compromised by infostealer malware or in a data breach, allowing them to take immediate action to secure accounts and prevent unauthorized access.
3. How do Data Breaches occur and what are their impacts?
Answer: Data breaches happen when unauthorized individuals access confidential data without permission, often through hacking, e.g. the use of malware like infostealers, account take-over, or phishing scams. The impacts include financial losses, legal consequences, damage to organizational reputation, and loss of customer trust. For individuals, breaches can result in identity theft and financial fraud, which can have enormous and lasting financial and legal consequences.
4. Are password managers safe from infostealer malware?
Browser-based password managers like those integrated within Chrome, Firefox, Safari, Brave, etc, are highly vulnerable and indeed one of the main targets of infostealer malware. These password managers work by storing your passwords in cleartext (i.e. without any encryption) on your computer, which means they can be copied and exfiltrated if your computer is compromised. Web-based password managers like LastPass or 1Password are not directly compromised by infostealer malware, but if you save your master passwords in a browser-based manager, hackers could then obtain your master password using an infostealer.
5. How can organizations protect themselves from credential compromise due to infostealer malware?
Organizations should educate employees about cybersecurity practices, such as avoiding password reuse and identifying malware sources like phishing emails. Organizations should also implement compromised credential screening or compromised password screening, multi-factor authentication, and NIST compliance.
6. How are Infostealers evolving with technologies like Optical Character Recognition?
Answer: Infostealers are becoming more sophisticated by incorporating technologies such as Optical Character Recognition. OCR enables malware to extract text from images, allowing infostealers to automatically harvest sensitive information found in screenshots or photographs, such as IDs or cryptocurrency keys. This evolution increases the scope and efficiency of data theft.
7. What is Credential Stuffing and how does it work?
Answer: Credential stuffing attacks involve cybercriminals using lists of compromised credentials—typically obtained from previous data breaches—to gain unauthorized access to user accounts. Attackers automate the authentication requests, enabling them to try huge lists of credentials until they find one that works. This can lead to further account compromises and data breaches.
AUTHOR
 Dylan Hudson
Dylan Hudson
Dylan leads the Threat Research team at Enzoic, developing and implementing cutting-edge threat intelligence infrastructure to help protect users and organizations from cyberattacks. When not at work, he can be found hiking and biking in the Rocky Mountains or playing traditional Celtic music on various stringed instruments.