With compromised password detection, custom password dictionary, fuzzy matching with common character substitutions, and continuous ongoing monitoring; enterprises can easily adopt NIST password requirements and eliminate vulnerable passwords in Active Directory.
Organizations can adopt NIST password standards to screen for weak, commonly-used, expected, and compromised passwords. Then they can check the password at the time it is created or reset, and monitor it daily against a real-time compromised password database.
NIST 800-63B:
…verifiers SHALL compare the prospective secrets against a list that contains values known to be commonly-used, expected, or compromised… The list MAY include, but is not limited to:
– Passwords obtained from previous breach corpuses.
– Dictionary words.
– Repetitive or sequential characters (e.g. ‘aaaaaa’, ‘1234abcd’).
– Context-specific words, such as the name of the service, the username, and derivatives thereof.
Many organizations are trying to adopt NIST 800-63b password standards but are struggling with the workload associated with it. Automated password policies can help simplify the implementation of NIST password standards without creating a lot of additional burdens on the IT team.
Here are some automated password policy options we recommend for NIST compliance and why organizations should adopt them.
The average person reuses each password as many as 13 times. Most people know better than to reuse passwords, but struggle to recall unique passwords for all of their personal and work accounts. Cybercriminals rely on this lax behavior and prey upon the vulnerabilities caused by password reuse. This is why compromised passwords are responsible for 81% of hacking-related breaches according to the Verizon Data Breach Investigations Report.
IT and Security teams are fighting back with compromised password screening. For example, some IT organizations occasionally download static password blacklists off the Internet and then periodically monitor their passwords against those lists. That is a significant first step, but those lists are typically only 10-20% of the common passwords that attackers use, so they provide limited protection. Additionally, since those lists require manual updates, it doesn’t protect organizations from any recent breach lists.
Screening passwords against a consistently updated list is critical. Attackers are frequently using the freshest exposures they can find because they know the more recent exposures will result in more successful outcomes. If an organization only uses old password blacklists, they are giving attackers a much larger attack window to take over an employee account.
Enzoic for Active Directory is the first product to introduce the ability to do continuous password monitoring against a proprietary password database of previous breach corpuses that is refreshed every day. Enzoic for Active Directory is a NIST 800-63b compliant password solution that uses a password filter to screen passwords being saved. It then continues to monitor the password daily to ensure it doesn’t become unsafe while it is in use.
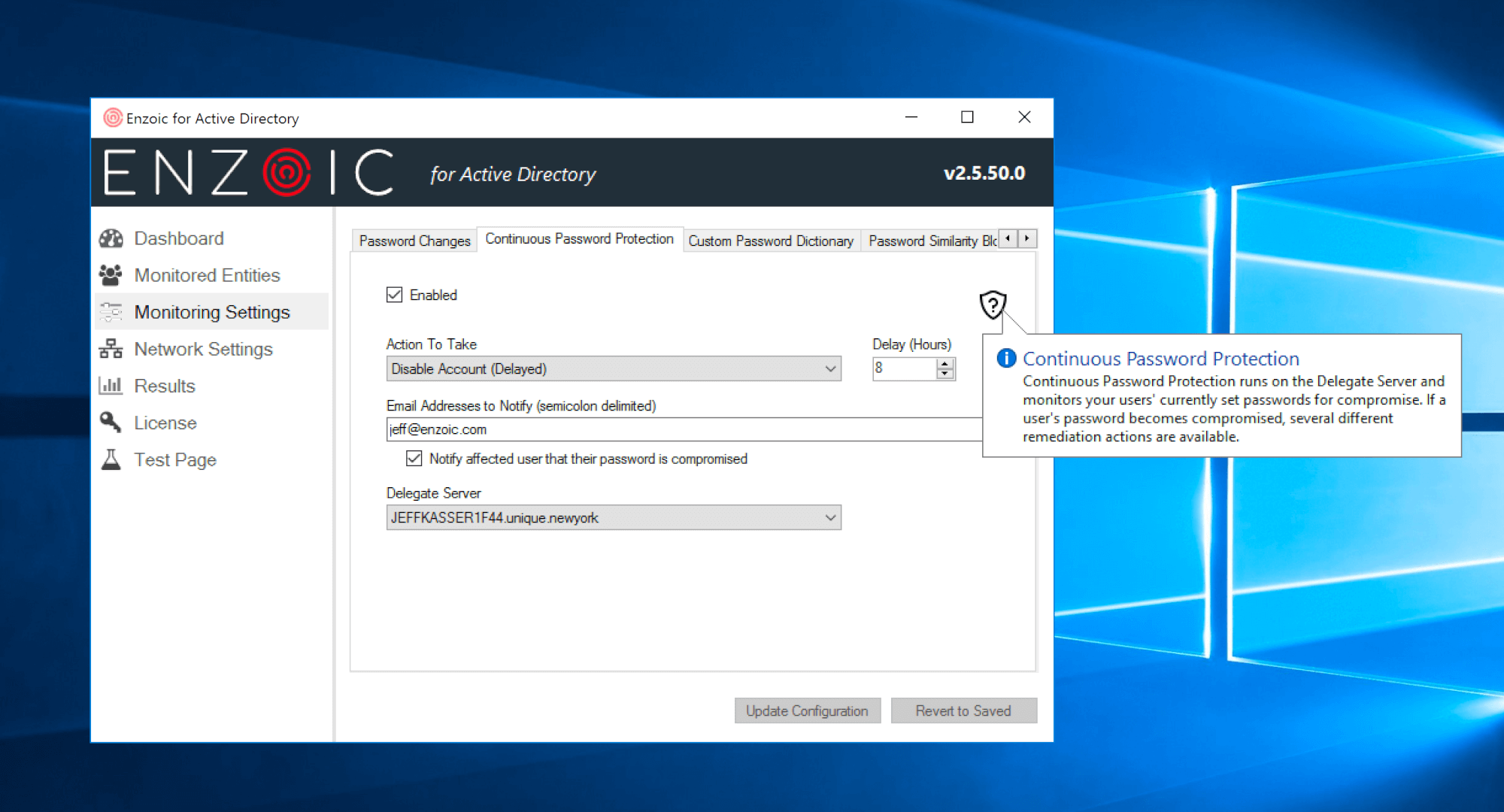 Enzoic for Active Directory: Screen for Compromised or Exposed Passwords Daily
Enzoic for Active Directory: Screen for Compromised or Exposed Passwords Daily
Many employees use weak or common passwords. Often they are completely unaware of it because they’ve satisfied password policies based on traditional algorithmic password complexity rules. For years the security industry has been trying to educate employees, yet still haven’t been able to secure this vulnerability. Many organizations are now choosing to take this burden off their employees and automating password policies to include screening for normal human limitations and behavior when it comes to passwords.
It starts with preventing common dictionary words. Every English-language word can be found in cracking dictionaries so organizations should prevent employees from using basic dictionary words in isolation. Pairing common words with other words, special characters and numbers can be allowed with appropriate character lengths. Additionally, organizations should block repetitive characters or sequential characters (for example: aaaaaa, 111111). Lastly, there are the most common passwords that attackers know some people will use so organizations should be blocking common passwords (for example: 123456, 12345678, qwerty, abc123, password1, iloveyou, etc.)
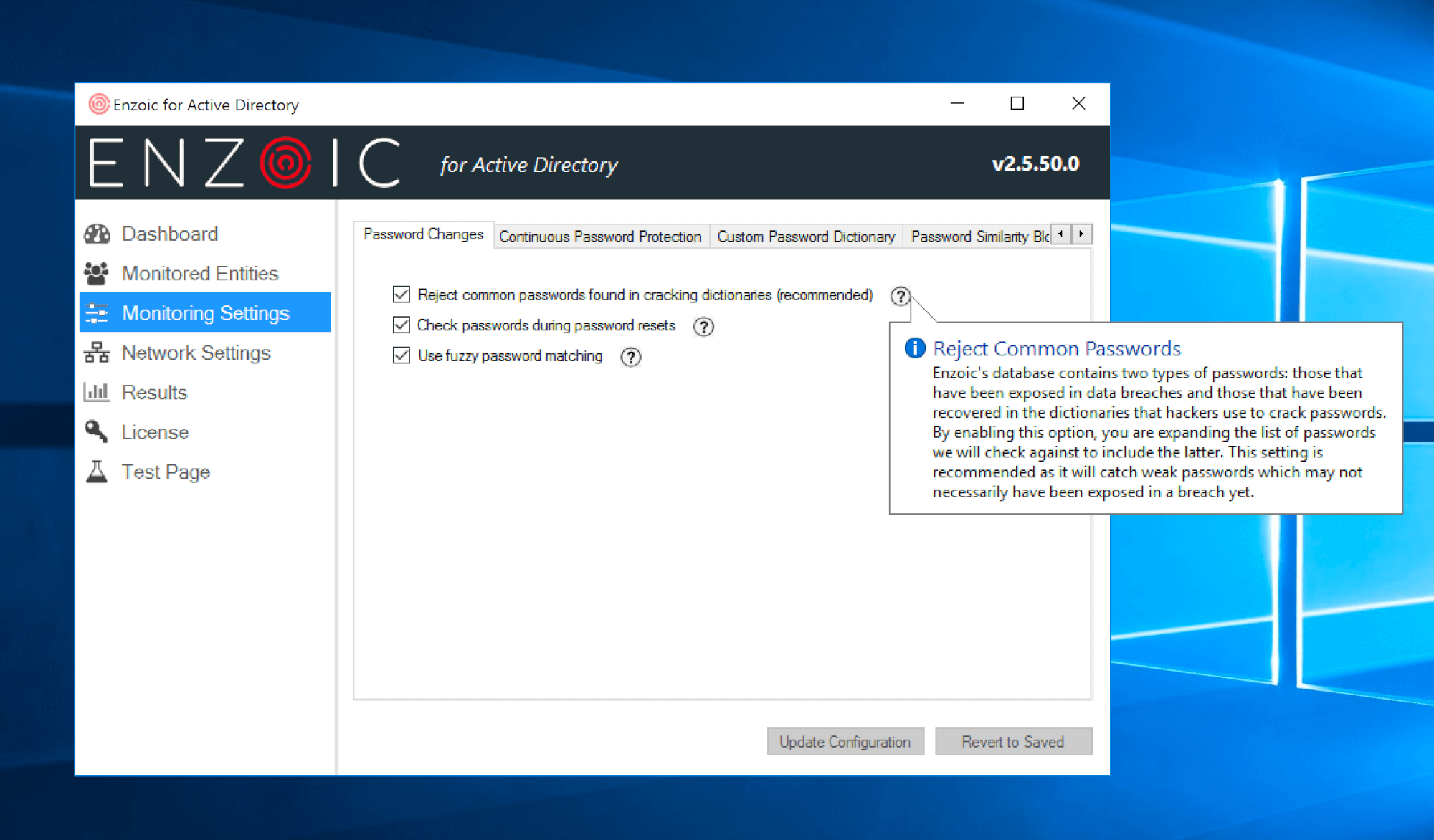
Most employees will also create or reuse passwords that are context-specific or expected. This can be expected passwords in the form of a root password that gets changed by just a few characters or even just capitalization. Once again, attackers know that this is a common practice on any system with users logging in, so organizations also need to prevent these expected passwords and their various forms.
Organizations should also deploy fuzzy password matching against the entries in their password blacklist. The reason why fuzzy matching is important is if your password is recently exposed online from another site, an attacker will choose to try patterns of that password. They will be highly successful in that endeavor because most people use patterns when selecting their passwords. Fuzzy password matching checks for multiple variants of the password, including case sensitivity as well as common substitutions such as leetspeak and password reversing.
For example: If your exposed password is “HolidayVacation1”, attackers will usually try variations such as:
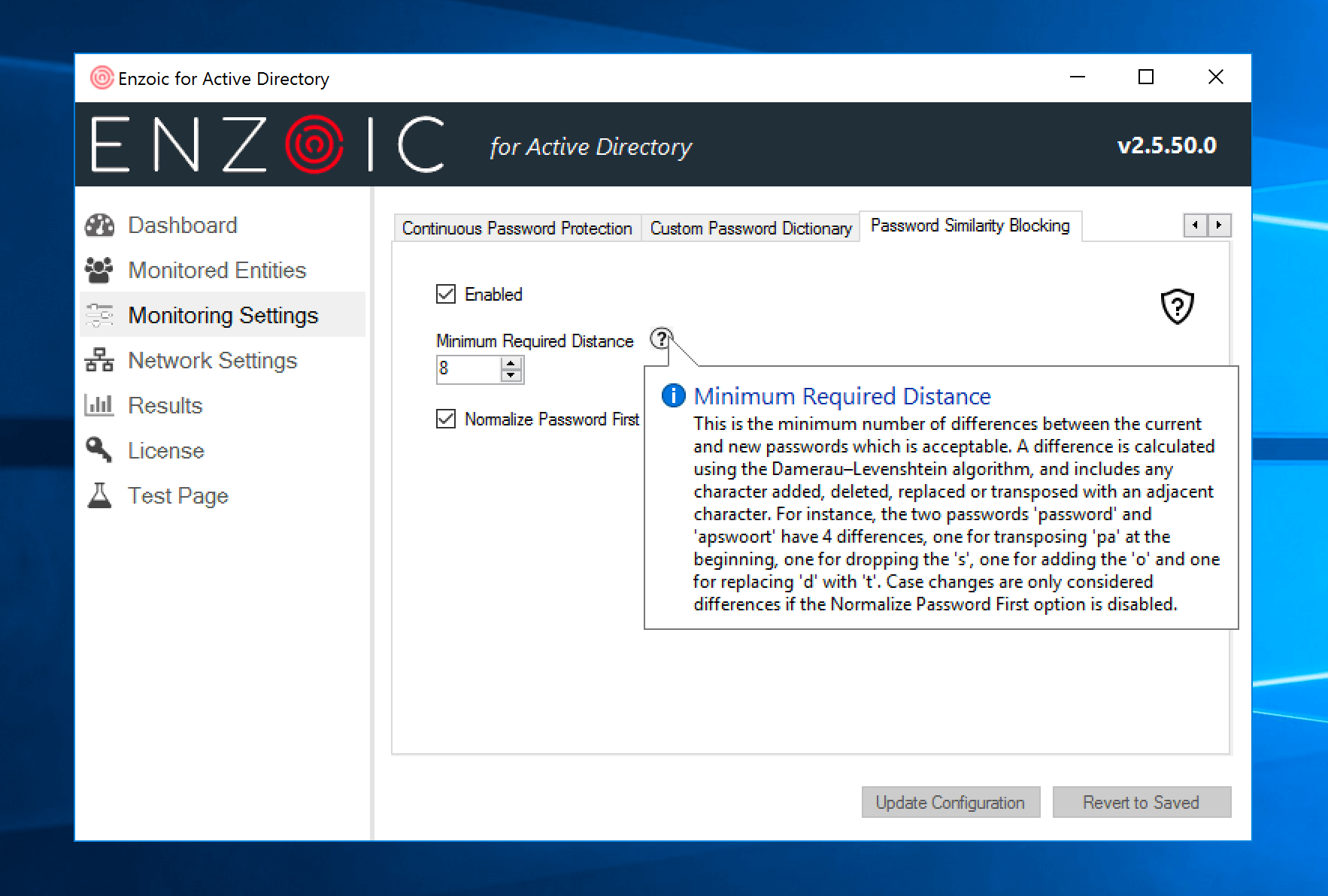
Another common employee password behavior that attackers exploit is using one root password and then using various iterations of it. This practice makes it easier for the employee to remember their password, but unfortunately, it also makes it easy for bad actors to figure it out. With this in mind, it is important for organizations to implement password similarity blocking. With password similarity blocking, new passwords are screened by similarity to a former password using the Damerau-Levenshtein distance.
For example: If your compromised password is “HolidayVacation2023” attackers usually try iterations like:
In Enzoic for Active Directory, the systems admin can determine the amount of difference (called distance) that will be required between the old password and the new password. With this password policy, the minimum number of differences would be 1 and the maximum number of differences for this rule would be 8. Companies and organizations have varying opinions on how many characters should be different, including transpositions, between old and new passwords. This configuration allows them to adjust it to the right level for their business.
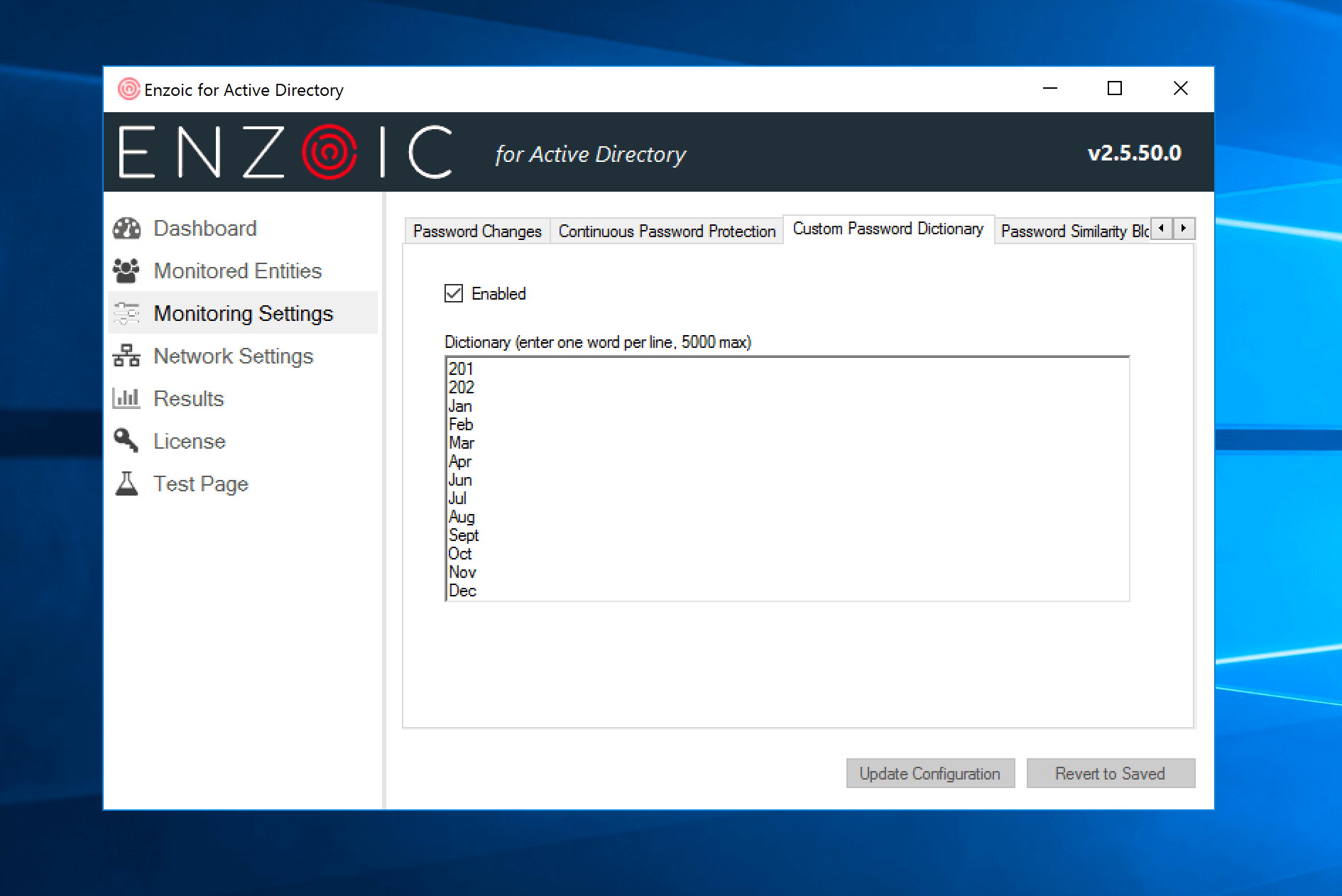
Savvy cybercriminals will also attempt to use context-specific passwords to gain access to Active Directory accounts. They know that companies that have headquarters in Boston will be more likely to have employee passwords that include “GoPatriots” due to the New England Patriots. They know that since many organizations enforce quarterly forced password resets, many employees will include seasons in their password like “Winter2019” and they know that many people include their company or product name in their password as well. Attackers exploit context-specific passwords because they are commonly used by employees. To combat this, companies need the ability to create a filter for a custom password dictionary.
With Enzoic for Active Directory, organizations can add up to 5,000 custom passwords stored locally that will be screened and blocked at creation. These words can be a local sports team, years, product names, company names, office locations, etc. Custom passwords are partially matched and case insensitive so any password that includes that word would be blocked. These can also be optionally fuzzy matched if you have fuzzy matching turned on.
For example: If your customer password dictionary includes the word “GeneralElectric”, users would not be allowed to use that word in any password so a password like “ILovegeneralElectric” will be blocked.
How Does Automating Password Policies Help the IT Team?
The goal of automation is to allow IT to set up the password policies and then just let them run. When an existing password becomes vulnerable, the remediation steps are automated instead of needing manual intervention by an Admin or Helpdesk.
Some organizations use password policy enforcement tools that handle one or some of these password policies, but the most recent version of Enzoic for Active Directory can meet all the NIST criteria. There is no additional manual work required. Enzoic for Active Directory serves as a comprehensive, automated password blacklist that filters for weak, commonly-used, expected, and compromised passwords.
Additionally, because organizations have unique needs, automated responses can be customized when compromised or weak passwords are found. The organization can select the appropriate automated action—ranging from prompting the user to change their password to disabling the account. These remediation steps can be set to kick-in immediately or after a predetermined delay. Alerts can also be sent to the user directly and/or an admin or helpdesk so the right individuals are kept informed.
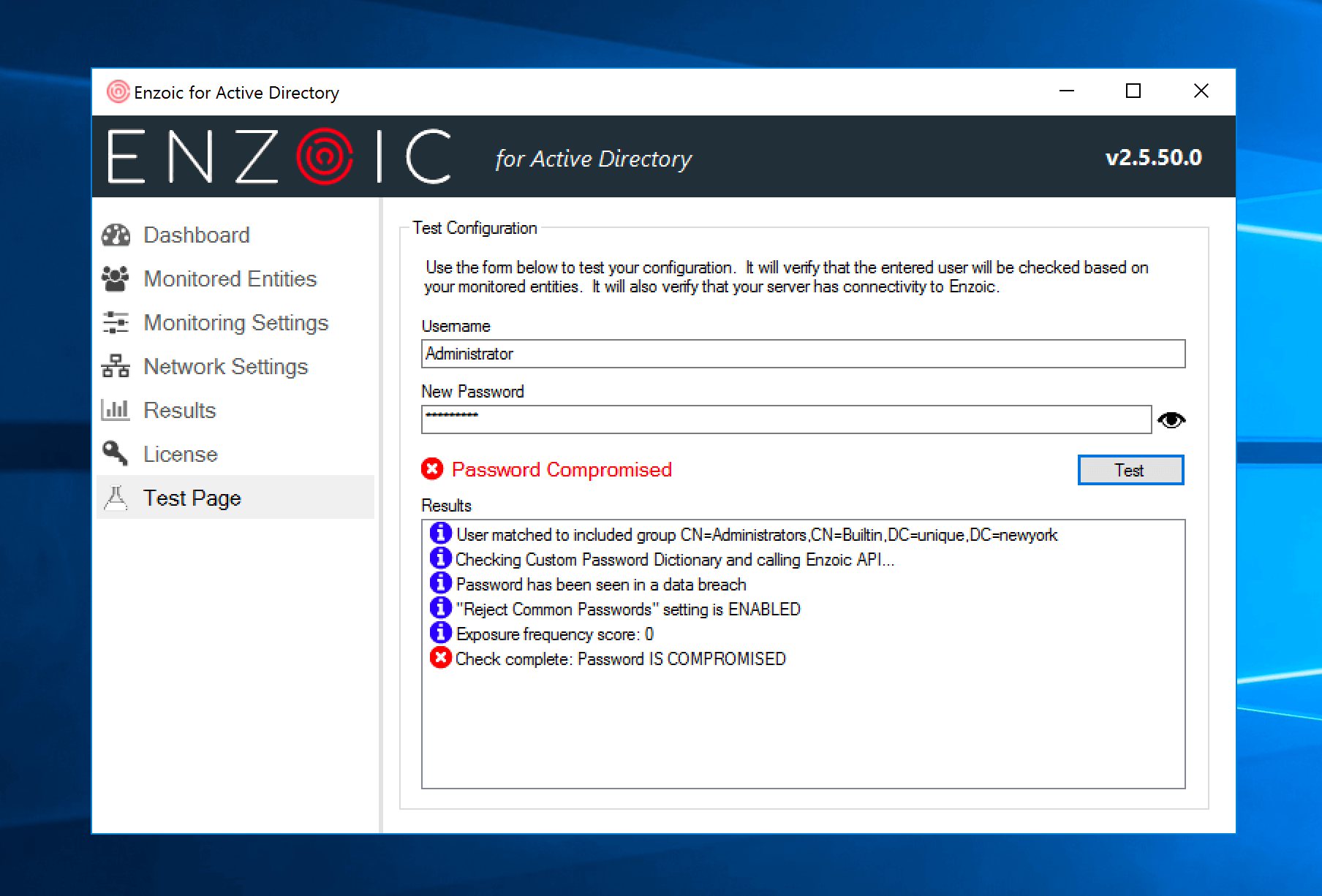
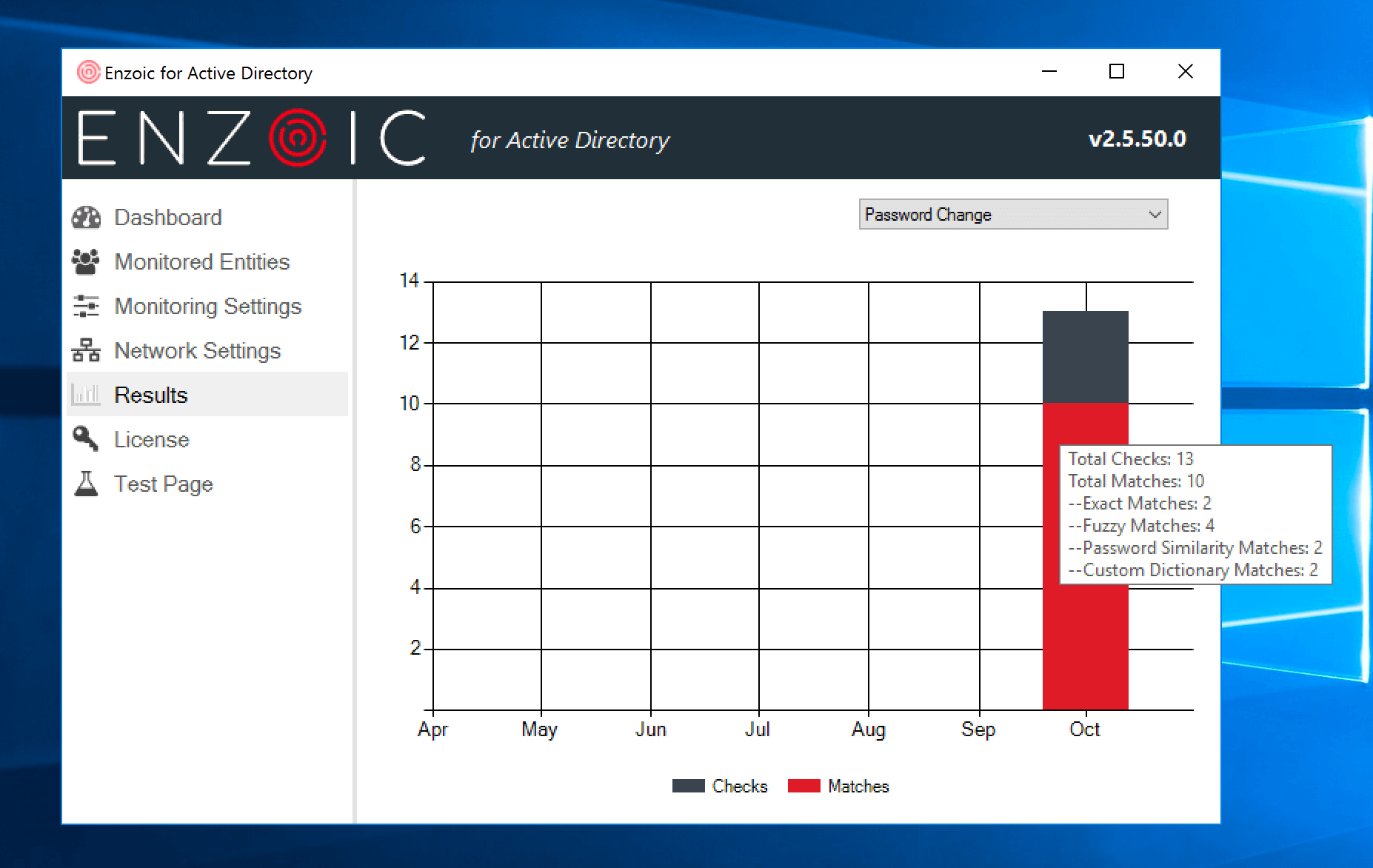
What Type of Visibility into Password Screening is Available?
Enzoic for Active Directory has also incorporated additional insights into the product. It has enhanced usage tracking so Active Directory administrators can see the total number of detections, including the number of detections due to fuzzy matching, local dictionary, or password similarity matching. With log files now stored in a JSON format, outside consumption by SIEM and log management tools can help streamline reporting.
What Installation is Required?
Enzoic for Active Directory runs on each domain controller so it can check every password wherever it is being created; however, it only needs to be configured once. All of its configuration settings are stored in Active Directory itself and automatically shared across other domain controllers to make it easy. With the installation wizard, it is easy to install so you can get it up and running fast. Some customers have it fully implemented in 15 minutes, but of course, that depends on the complexity of your environment.
Automate Password Policy and Adopt NIST Password Standards
Enzoic for Active Directory enables quick-to-deploy automated password policy enforcement and daily exposed password screening. With fully automated weak password filtering, fuzzy password matching, password similarity blocking, and custom password dictionary filtering; enterprises can easily adopt NIST password requirements and secure passwords in Active Directory.
Contact info@enzoic.com to learn more about the benefits of Enzoic for Active Directory for automating password policy.
Start for free. Enzoic provides a clean user interface to screen for compromised passwords.
Experience Enzoic