News and warnings about data breaches and leaks abound at the moment, emphasizing the need for increased cybersecurity regardless of the industry. Microsoft’s Active Directory is often the perfect target for bad actors seeking to abuse compromised credentials.
Despite the frequency of compromised credentials being the cause of data breaches, most organizations do not know whether their users’ passwords are safe. If your company is not adhering to NIST guidelines, you may be in for an abrupt awakening.
This article seeks to explain just how big the problem of compromised credentials may be for a company like yours and to provide a benchmark based on Enzoic’s audit of over 1,000 corporate domains.
Results from the Enzoic audits showed nearly 20% of real-world corporate user accounts were weak or compromised, highly vulnerable to password attacks. The data is from a sample of business domains that had their users’ credentials securely scanned with Enzoic for Active Directory Lite. This service securely audits to help find weak and common passwords, passwords found in cracking dictionaries, and passwords that have been previously breached and exposed online.
Understanding the Findings
A sample of over a thousand corporate domains and a total of over 1.5 million user accounts were scanned and compared against the Enzoic blacklist of over 7+ billion exposed passwords.
The comparisons between these credentials and the blacklist were done locally on the client network, with no sensitive data leaving the authorized space so that all user privacy was intact.
Based on the low latency design of the service, blacklist comparisons were completed at a rate of 10 per second. This is an indication of how quickly unsafe passwords could be identified in these organizations.
The audits looked for two different categories of unsafe password: compromised and weak. A “compromised password” was defined as an exact password actually exposed in a prior data breach. A “weak password” is an exact password found in a cracking dictionary (that excludes those passwords that were actually exposed in a data breach). Distinguishing between these two categories allows for a better look into how severe the security threat is to an organization, but both categories are clearly unsafe.
-The data showed that of the users scanned, 19.8% of corporate users had unsafe passwords (figure A).
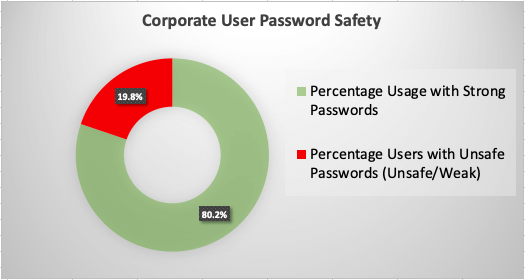
For corporate IT professionals and Active Directory administrators, the statistic of ~20% of passwords being unsafe should be immediately concerning. Many of the companies scanned in this collection most likely think that they are using strong password policies already.
If these statistics aren’t initially alarming to you, consider that it’s estimated that about 80% of all breaches are related to compromised credentials. Also, remember that it only takes a single breached set of credentials for a hacker to move rapidly into a network.
Stolen credentials are often the foothold that attackers use. A single password might be the entry point for data theft from a particular account or hijacking the entire network.
Looking Closer at Types of Unsafe Passwords
To better understand the problem, we looked at the split between weak and compromised passwords. Recall that “weak passwords” refer to those found in cracking dictionaries but not an actual data breach. The “compromised passwords” belonged to real users and were leaked in actual data breaches.
The data revealed that of those with unsafe passwords, just over 10% of those were using weak passwords while the 90% rest were using compromised passwords. See Figure B.
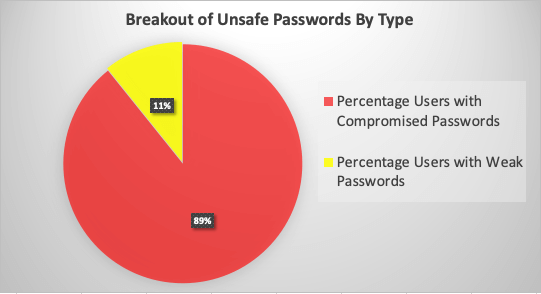
Some might wonder why there were so many more compromised passwords. While a cracking dictionary includes many variations (e.g., ‘fuzzy match’) of real-world passwords, the problem of password reuse is so common that passwords from actual data breaches have a much higher hit rate. This detail underscores the need to identify which passwords have already been compromised and do something about it.
Indeed, the password blacklist being compared with users’ credentials in Enzoic for Active Directory Lite is only a subset of what’s available with the full Enzoic for Active Directory experience. Checking users’ credentials against our passwords blacklist is just one of the tools that Enzoic offers to enhance your security posture.
In other words, what the results reveal is akin to the best-case scenario of how many passwords are unsafe within an average company. If the best-case scenario is that one in five users’ passwords are weak, just imagine how much larger the problem actually is.
Keep in mind too that in this data we are looking at averages. There is plenty of variation in the types of companies and the types of security that they are using, and some companies audited had substantially more than 20% of their employees’ credentials using unsafe passwords.
The way this information is obtained – namely, through password auditing – is a regular type of security practice, but traditionally a very burdensome one. It involves trying to brute force guess the passwords, a process that in the past might have taken anywhere from minutes to days to go through lists of passwords to see if they are vulnerable. But if Enzoic can create a blacklist that reverses password hashes in just minutes, that means a hacker can do it too. Weak and compromised credentials are thus a massive, immediate threat to the security of your company.
Actions You Can Take
The issue of password security has to do with individuals’ behavior as well as with organizational policy. It’s time for both top-down and bottom-up approaches to the problem.
Consider, as a first step, using Enzoic for Active Directory Lite to compare your own organization against the benchmark of 20% unsafe passwords discussed in this article.
Using this audit tool will allow your organization to get a quick snapshot of the domain’s password security state against the latest breaches and cracking dictionaries.
Next, understand that the free audit is a subset of the data that’s available in the full Enzoic for Active Directory service. Enzoic’s full database is substantially larger and draws from many areas, from the dark web to daily breaches, and is ever-evolving with both automated research and real human threat intelligence.
With the full Enzoic for Active Directory, there is a tremendous amount of additional functionality and tailoring your company can employ – like custom blacklists, fuzzy matching, root password blocking, and continuous password monitoring. Most importantly, the service becomes a seamless part of the environment preventing the need for periodic auditing. This helps ensure that your organization is up to NIST standards and kept as safe as possible.