Back to Blog
Credit Card Fraud: How Does It Work?
In this article, we’ll take a deep dive into some real-live techniques and scripts used by threat actors to commit credit card fraud. There are of course many ways to skin this proverbial feline, but it can be illuminating (possibly concerning) to see the actual steps involved. Let’s start right out with a step-by-step overview of the whole process, and then we’ll dive into some of the specific tools and methods that cybercriminals use in more detail.
Step 1: Card Compromise
The journey begins when a credit card is compromised through one of several methods:
- Data Breaches: Hackers penetrate company databases containing customer payment information. The healthcare industry has had a particularly large problem with this recently.
- Card Skimmers: Physical devices attached to legitimate card readers (like ATMs or gas pumps) that secretly capture card data when customers swipe their cards.
- Algorithmic Generation: Threat actors have written programs that generate potentially valid card numbers based on bank ID numbers, the leaked details of the card issuers’ own generation algorithms, and the Luhn algorithm (a checksum formula used to validate card numbers).
- Phishing: Creating fake websites or sending deceptive emails that trick users into entering their card details.
- Physical Theft: The tried-and-true stealing of wallets or purses containing physical cards.
Step 2: Underground Market Distribution
Once obtained, the compromised card information enters the criminal market:
- Dark Web Marketplaces: Card details are listed for sale on underground forums and marketplaces, often priced according to the card type, issuing country, and whether they’ve been verified.
- Bulk Sales: Unverified cards are typically sold in bundles at lower prices (often $5-20 per bundle of 100+ cards).
- Organization by BIN: Cards are frequently organized by Bank Identification Number (first 6 digits), allowing buyers to select cards from specific banks or regions.
Step 3: Card Verification
Before committing to large transactions, criminals verify which cards are still active:
- Micro-transactions: Small charges are attempted to confirm the card is active without triggering fraud alerts.
- Subscription Services: Free trial signups requiring card details are used to verify card validity without actually charging the card.
- Automated Testing: This process is typically conducted using specialized “card checking” scripts, as we detail in the next section.
Step 4: Monetization of Verified Cards
Once verified as active, cards increase significantly in value and can be used in several ways:
- Value-Added Resale: Verified cards command much higher prices ($20-200 per card, depending on the credit limit and card type).
Online Purchases: Cards are used to buy high-value goods online (electronics, gift cards, luxury items) that can be resold for cash.
- Card Encoding: The digital information is encoded onto blank physical cards with magnetic stripes, creating counterfeit cards for in-store purchases.
- Cash Withdrawals: Encoded cards may be used at ATMs to withdraw cash directly (usually requiring the PIN, which may have been captured with the card data).
Step 5: Erasing One’s Steps
The final stage involves converting fraudulently obtained goods or funds into untraceable cash:
- Reshipping: Purchased items are sent to “drops” (addresses controlled by accomplices) before being resold.
- Cryptocurrency Conversion: Funds are often converted to cryptocurrencies to obscure the money trail.
- Money Laundering: Individuals who help move funds through their own accounts in exchange for a percentage.
- Gift Card Conversion: Purchasing gift cards with stolen credit cards, then selling them at a discount for cash.
Throughout this entire process, fraudsters are in a constant race against time as they must complete their operations before the legitimate cardholder notices unauthorized charges and notifies the bank of potential fraud, or the issuing bank detects unusual use patterns and rejects the transaction or cancels the card.
A fraudster’s photo displaying his credit card blanks used for encoding stolen numbers (and what is presumably the ill-gotten gains).
Inside a Card Testing Operation
When cybercriminals obtain credit card information—whether through data breaches, reader skimming (e.g. at gas pumps), phishing, or purchasing them on dark web marketplaces—they need to verify which cards are still valid and active; otherwise, they are useless and open the user up to suspicion for trying too many disabled cards (we all know how it feels to have your credit card get declined– imagine this happening 200 times in a row). This process involves customizable software tools and techniques designed to bypass security measures and validate the stolen card data.
Carding Frameworks
Modern credit card fraudsters rely on specialized software frameworks to automate their operations. Automation is critical for profitability, as these operations are time-sensitive, and may require sifting through large amounts of data that would be prohibitive to test by hand. These tools are quite sophisticated, featuring user-friendly interfaces and modular designs that often rival the consumer software industry for UI functionality. The designs typically allow for quick adaptation as a counter-security strategy, as fast evolution is one the most effective strategies that cyber criminals can leverage…always trying to stay a step ahead of the developers and law enforcement.
Some of the most common frameworks include:
- Card Checkers: Automated tools that test stolen credit card numbers against legitimate payment processors like Stripe and Braintree
- Fraud Panels: Web-based dashboards that manage card-testing operations, often including valid card tracking and proxy server rotation
- BIN Checkers: Tools that analyze Bank Identification Numbers (BINs) to determine card details like issuing bank and card type (a BIN is typically the first 4 to 6 digits of a credit card number)
Okay, let’s examine how the initial verification works, using a real ‘config’ file shared by cybercriminals. Config files are used to specify the parameters and function of a larger automation framework.
- Setup and Configuration: The fraudster configures their carding tool with specific parameters targeting a legitimate website (in our example, a popular form builder service “wpforms.com” ). This small excerpt from the start of the config shows some of the parameters to be configured:
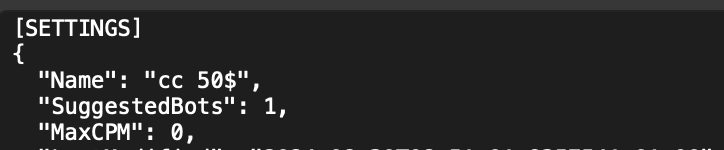
- Identity Generation: The tool automatically creates convincing fake identities using services like randomuser.me, complete with names, emails, and addresses.
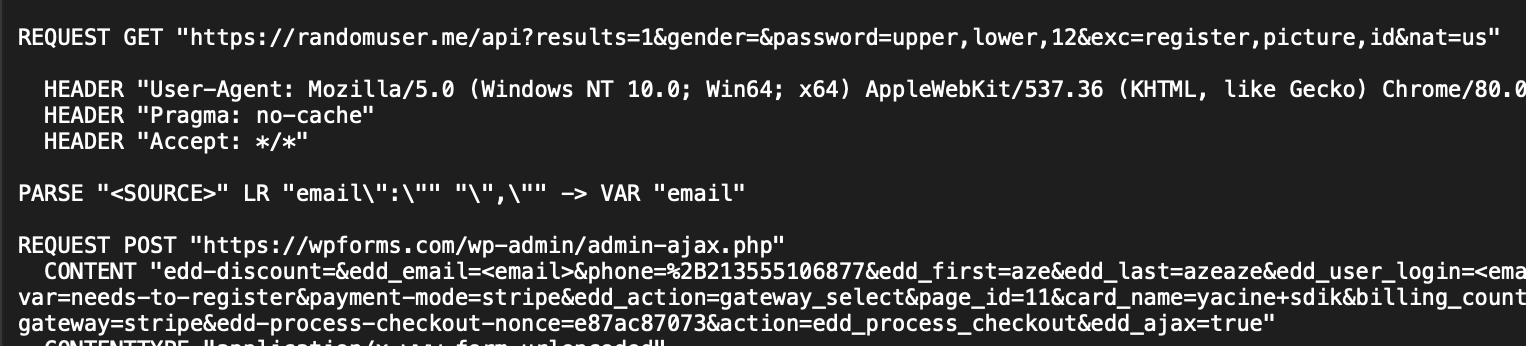
- Account Registration: The tool registers a new account on the target website using the generated identity, often applying discounts (in our example, “SAVE50” for 50% off) to minimize the charge amount.
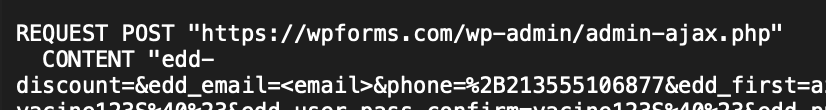
- Payment Attempt: The tool submits the stolen credit card details to process a small payment, typically using the legitimate payment API of the target site.
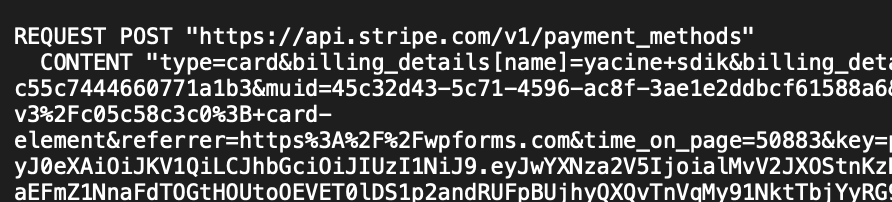
- Response Analysis: The system parses the response to determine whether the card is valid based on specific success or failure messages.
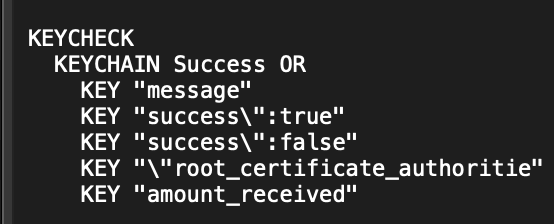
- Scaling Up: This process is repeated across hundreds or thousands of cards in rapid succession, often using rotating proxies to avoid detection.
This example demonstrates several techniques to evade detection and speed up the process:
- Anti-Detection Mechanisms: Random identity generation, custom user agents, and controlled request timing to mimic human behavior
- API Integration: Direct integration with payment processors like Stripe to process transactions
- Modular Design: Configuration-based approach allowing the script to be quickly adapted for different target websites
- Response Parsing: Logic to interpret transaction results and categorize cards as valid or invalid
What makes these tools particularly concerning is their accessibility. Complete carding frameworks are sold on underground forums, while configuration files (like the one analyzed) are often shared in private Telegram channels, democratizing fraud capabilities among less technical criminals.
The Economics of Card Testing
For cybercriminals, card testing is a numbers game. A typical operation might test thousands of stolen cards, expecting only a small percentage to be valid. Even with a 5-10% success rate, the operation remains profitable due to:
- Low Entry Costs: Carding tools are relatively inexpensive, with many configurations shared freely. There is of course no honor among thieves, who constantly steal and trade copies of carding software as well.
- High Potential Returns: Successfully verified cards are either used for larger fraudulent purchases or sold at premium rates on dark web marketplace. We can see a single card number can fetch $12.99 in the below screenshot from a ‘carding’ marketplace.
How Organizations Defend Against These Attacks
Payment processors and e-commerce platforms can employ several defensive measures:
- Velocity Checks/Rate Limits: Detecting unusual numbers of transactions from a single source (although threat actors often get around this using the techniques discussed above)
- Device Fingerprinting: Identifying automated tools based on their technical characteristics – this can get pretty advanced, including using data points like screen size of the login device, typing and mouse patterns, even what font libraries may be available on the device. Of course, threat actors are always trying new ways to spoof these and camouflage themselves.
- Dark Web Data Monitoring: cybersecurity vendors produce intelligence that can help organizations flag these numbers as soon as they hit the market.
- Machine Learning: Analyzing transaction patterns to spot anomalies. This is actually one of the better uses of “AI” in security technology these days. ML models can be trained to identify high-risk patterns across many, many data points and produce additional risk signals to enact further security measures like SMS verification or rate-limiting.
- CAPTCHA and Anti-Bot Systems: Requiring human verification for suspicious transactions. Threat actors hate identifying which photos have traffic lights in them too, and of course this prevents automatic scripts from being effective.
- Address Verification System (AVS): Matching billing addresses with card issuer records
Self-Defense For the Individual Cardholder
While organizations continue to enhance their security measures, consumers should also take proactive steps:
- Monitor Your Statements: Review credit card statements regularly for unfamiliar charges, even small ones– a thief may make many small transactions across many cards to avoid detection.
- Enable Transaction Alerts: Set up notifications for all card transactions. It’s hard to separate signal from noise in today’s world of constant alerts and alarms, but this is probably one of the more important ones to consider implementing. It’s hard to go back through long statements, but screening each transaction as it occurs can be an easier lift.
- Use Virtual Cards: Consider using virtual card numbers for online purchases, no need to cut up a physical card and wait for a new one in the mail if one is compromised.
- Freeze Unused Cards: Many banks allow you to “freeze” cards when not in use. Freezing your credit unless you plan to use it is also a good idea in general.
- Report Suspicious Activity: Report even small unauthorized charges immediately to the bank, as they can investigate further and take action.
In Conclusion:
The sophistication of modern credit card fraud tools highlights the accessible nature of this cybercrime venue. What was once the domain of technically-precocious hackers has become accessible to a wider audience through ready-made tools and easily shared configurations to handle many scenarios. Understanding these techniques helps both consumers and organizations better prepare their defenses against these persistent threats.
For security researchers and professionals, these insights underscore the importance of continuous monitoring and adaptation in the ongoing battle against financial fraud.




