Elevate Your Password Security
With compromised credentials the #1 cause of a data breach, securing passwords is more crucial than ever. Microsoft Entra ID (formerly known as Azure Active Directory) is one of the tools many organizations rely on to protect their passwords, but is it enough?
Despite its popularity, Microsoft Entra ID has significant limitations that can leave systems vulnerable to attacks. This blog will explore these restrictions and explain why Enzoic provides a more comprehensive solution for password protection than Microsoft Entra ID.
Microsoft Entra ID is part of the Microsoft Entra product suite, designed to help organizations manage identity and access. One of its features is basic password protection, which tries to restrict users from setting weak or compromised passwords, but their approach falls short of fully ensuring that users consistently set and maintain strong, secure passwords. The system works by checking passwords against a banned password list and enabling administrators to create custom lists specific to their organizations.
On the surface, this approach seems like it would be enough. By blocking passwords associated with previous attacks against Microsoft, Microsoft Entra ID can help reduce the risk of employee account takeover. However, the static nature of this protection is limiting, with an incomplete exposed password dataset and the inability to continuously monitor passwords after creation.
Microsoft Entra ID’s password protection relies on a list of banned passwords, which is updated based on Microsoft’s internal telemetry and analysis. This approach has several critical weaknesses:
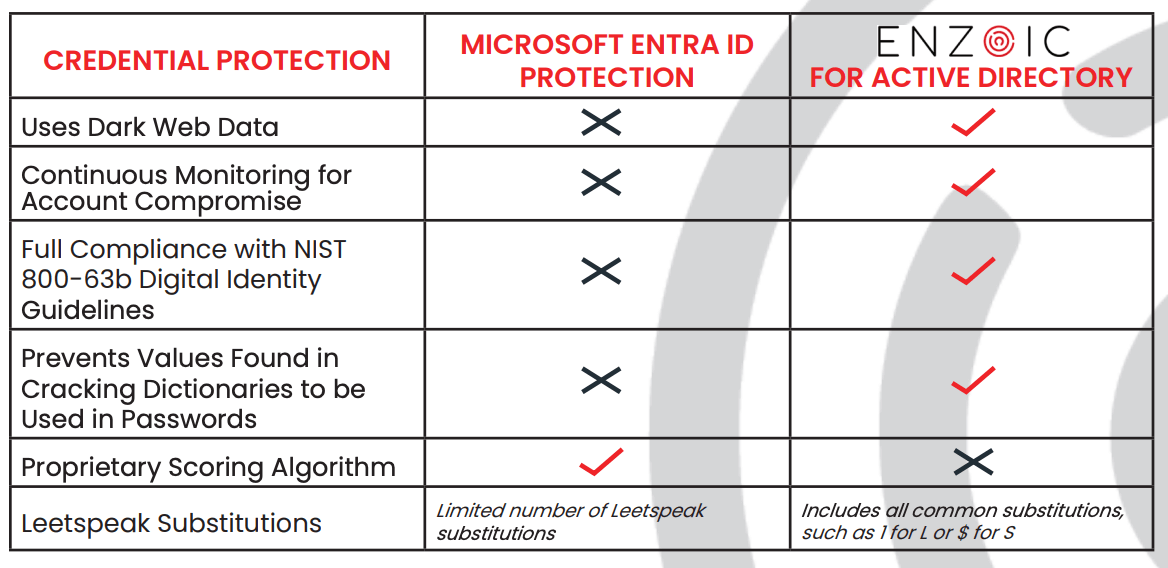
Organizations that rely solely on Microsoft Entra ID for password protection may find themselves vulnerable to several attack vectors:
In an environment where adversaries are increasingly logging in rather than hacking in, relying solely on static password protection solutions like Microsoft Entra ID is not enough. The limitations of Entra ID, including its limited scope of banned passwords and lack of continuous monitoring, leave organizations vulnerable to a range of attacks.
Enzoic for Active Directory provides a dynamic alternative by offering real-time password protection that continuously monitors for compromised credentials, aligns with industry best practices, and integrates seamlessly into hybrid environments. By adopting Enzoic, organizations can significantly enhance their password security and reduce the risk of account takeovers, ensuring that their systems remain secure against their top threat.
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.
Explore free for up to 20 users. Save hours of admin time and simply get started with a password monitoring solution.