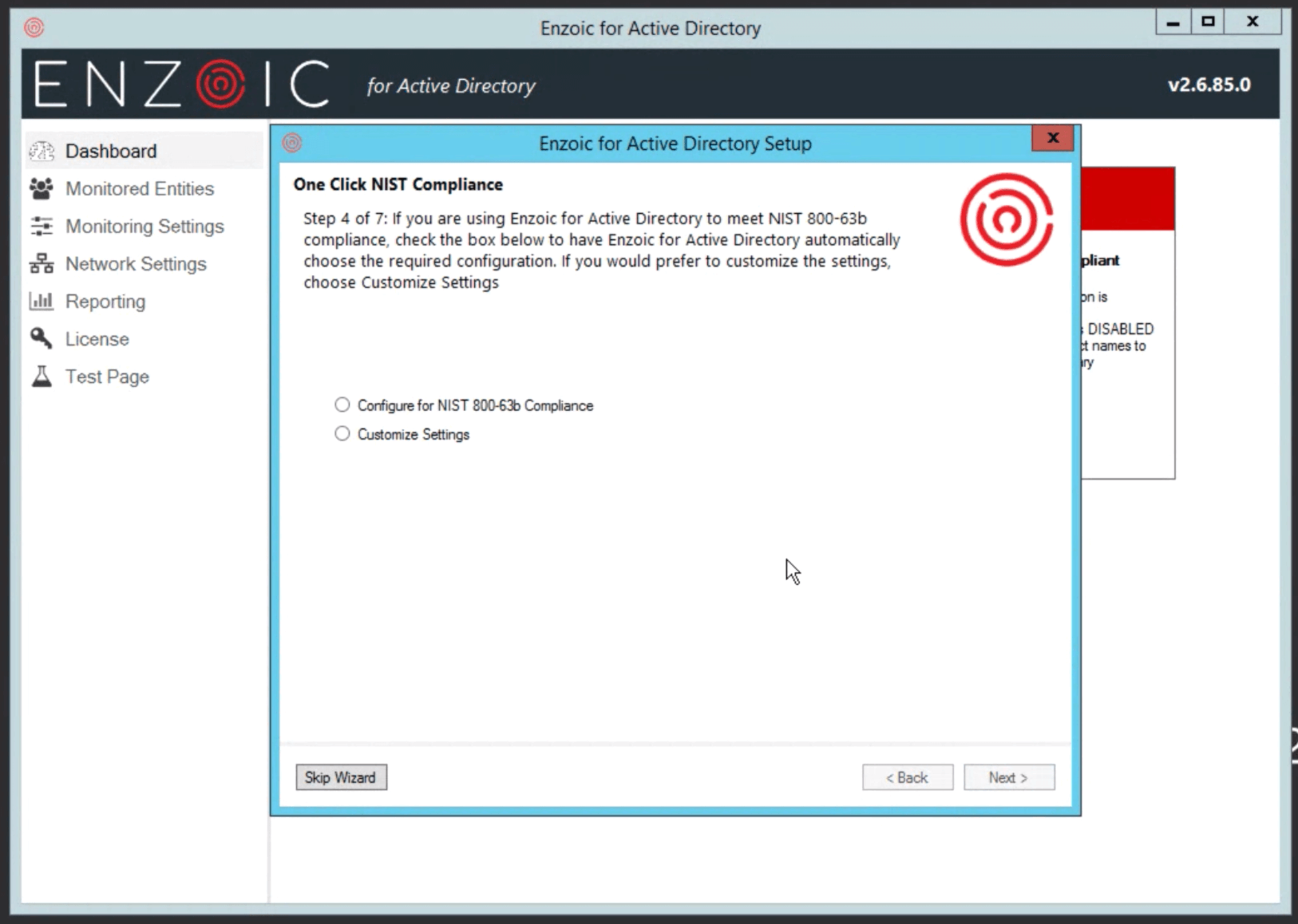
Introducing one-click NIST password standard compliance, user reporting which outlines users who are using compromised passwords, and root password detection to prevent users from using root passwords.
Microsoft’s Active Directory is used widely across companies and industries throughout the world and unfortunately, it is one of the key targets for bad actors. Many organizations are adopting the use of password blacklists or compromised password detection to help protect Active Directory accounts from account takeover. But static password blacklists are simply not enough because they get outdated too fast and attackers often use fresher lists to attack to increase their odds of success.
Modern organizations are moving to Active Directory plugins that automatically check for compromised passwords on a daily basis. The automation reduces the burden on their IT team from having to manually update static lists, while a daily refresh of continuously updated dark web data decreases the window for an attack.
With this in mind, Enzoic is introducing new features into Enzoic for Active Directory version 2.6. This version includes many unique features including easy one-click NIST password standard compliance in the setup wizard, user reporting which outlines users who are using compromised passwords, and root password detection to prevent users from using root passwords.
Please view our release notes below to see the newest features.
A new one-click wizard to guide the user through configuring the application options to ensure compliance with NIST password standards. This includes:
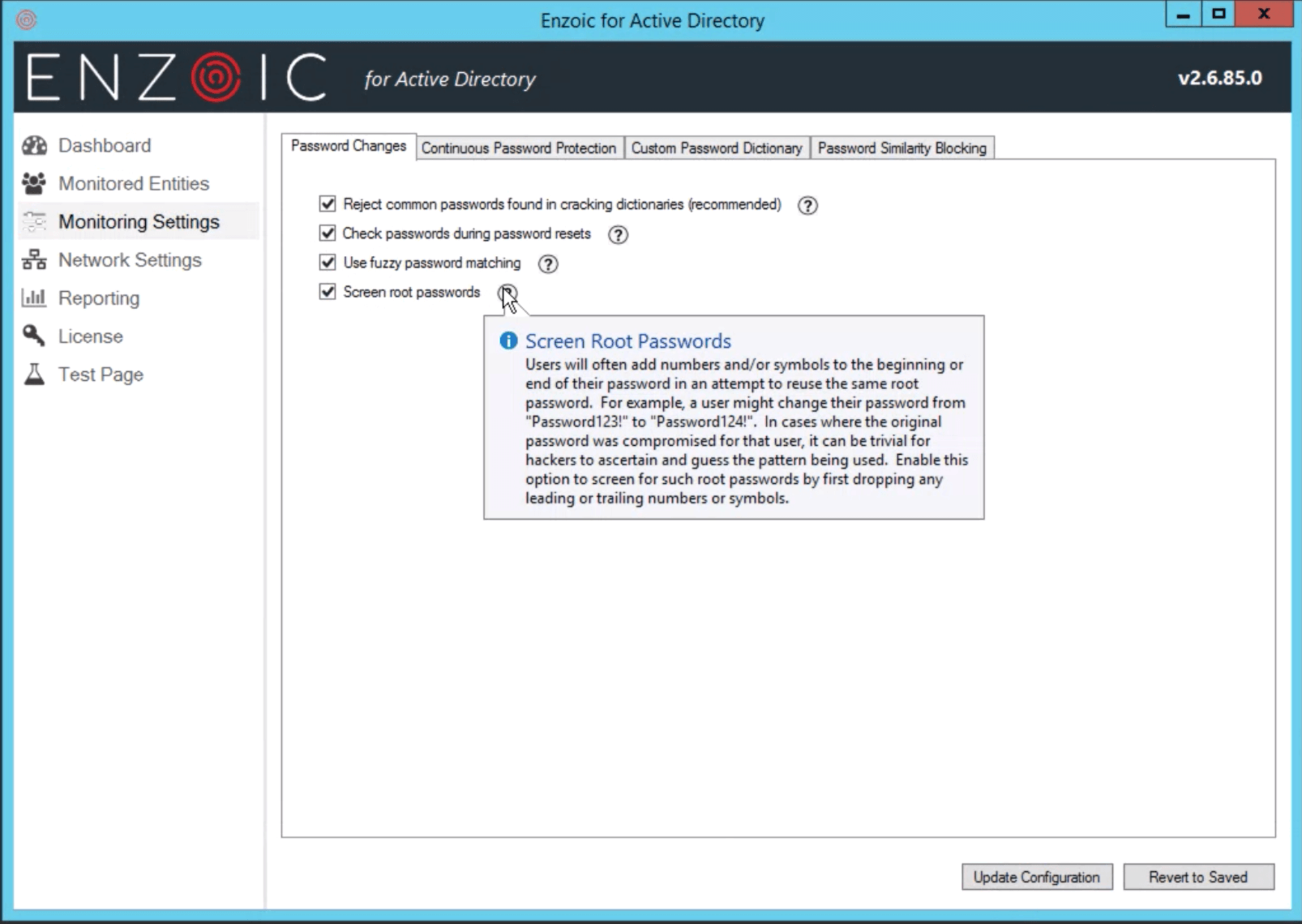
Root Password Detection optionally will check user passwords for so-called “root” passwords that are common or compromised. It does this by removing trailing numbers and symbols that users often will use to prefix or suffix a less secure password in order to meet complexity or uniqueness guidelines.
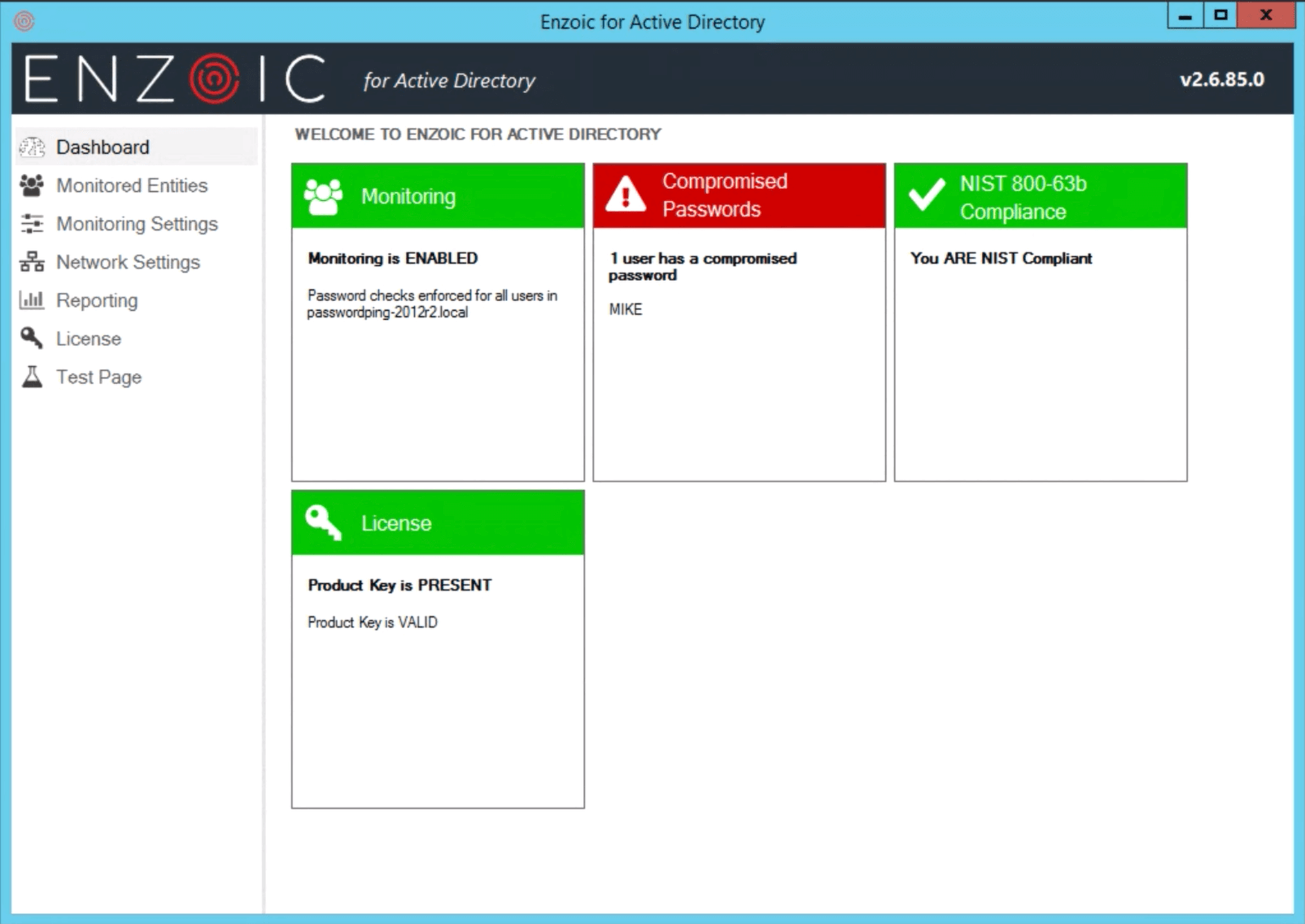
A dashboard widget that provides “at a glance” indication of whether the current settings are NIST compliant.
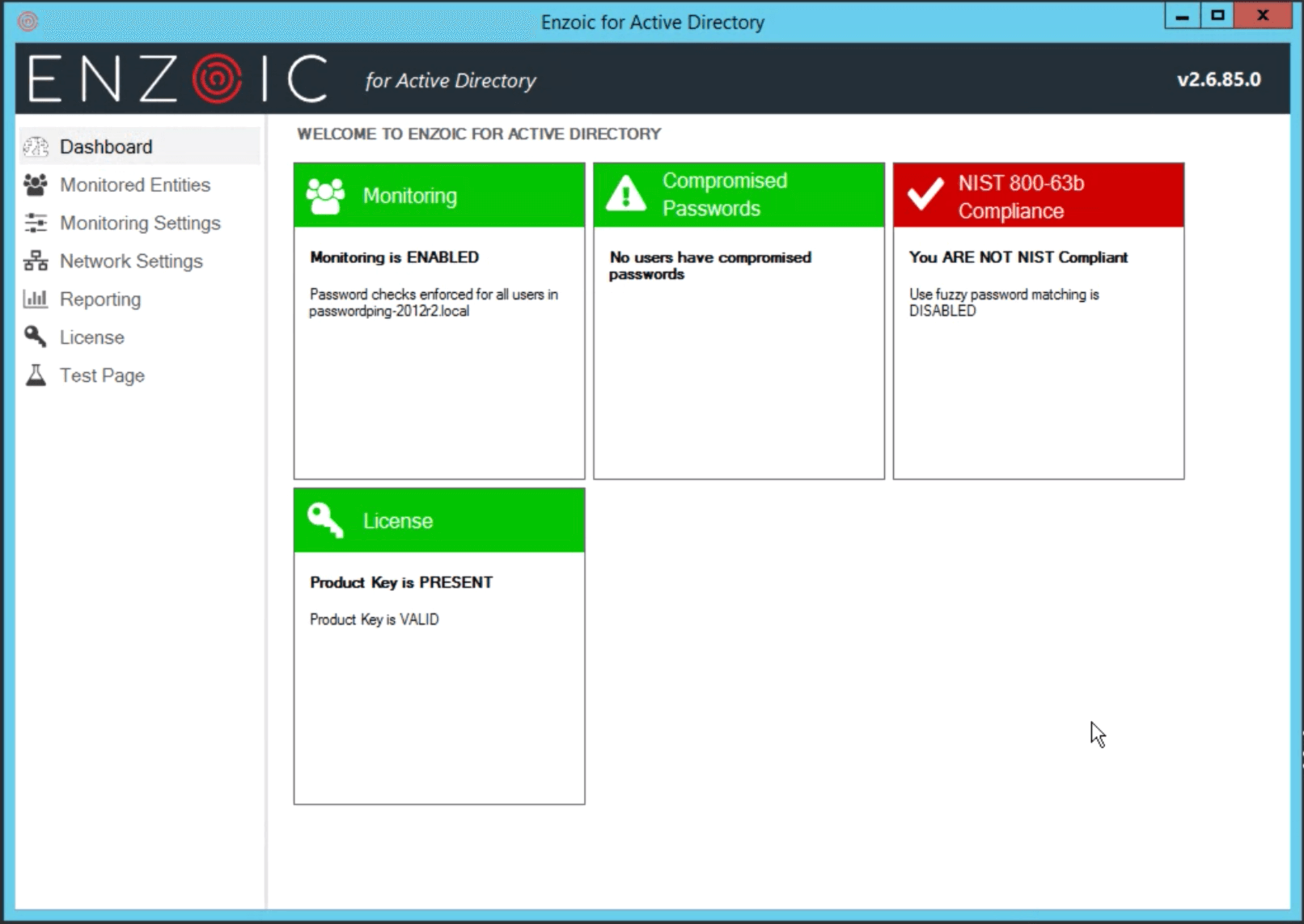
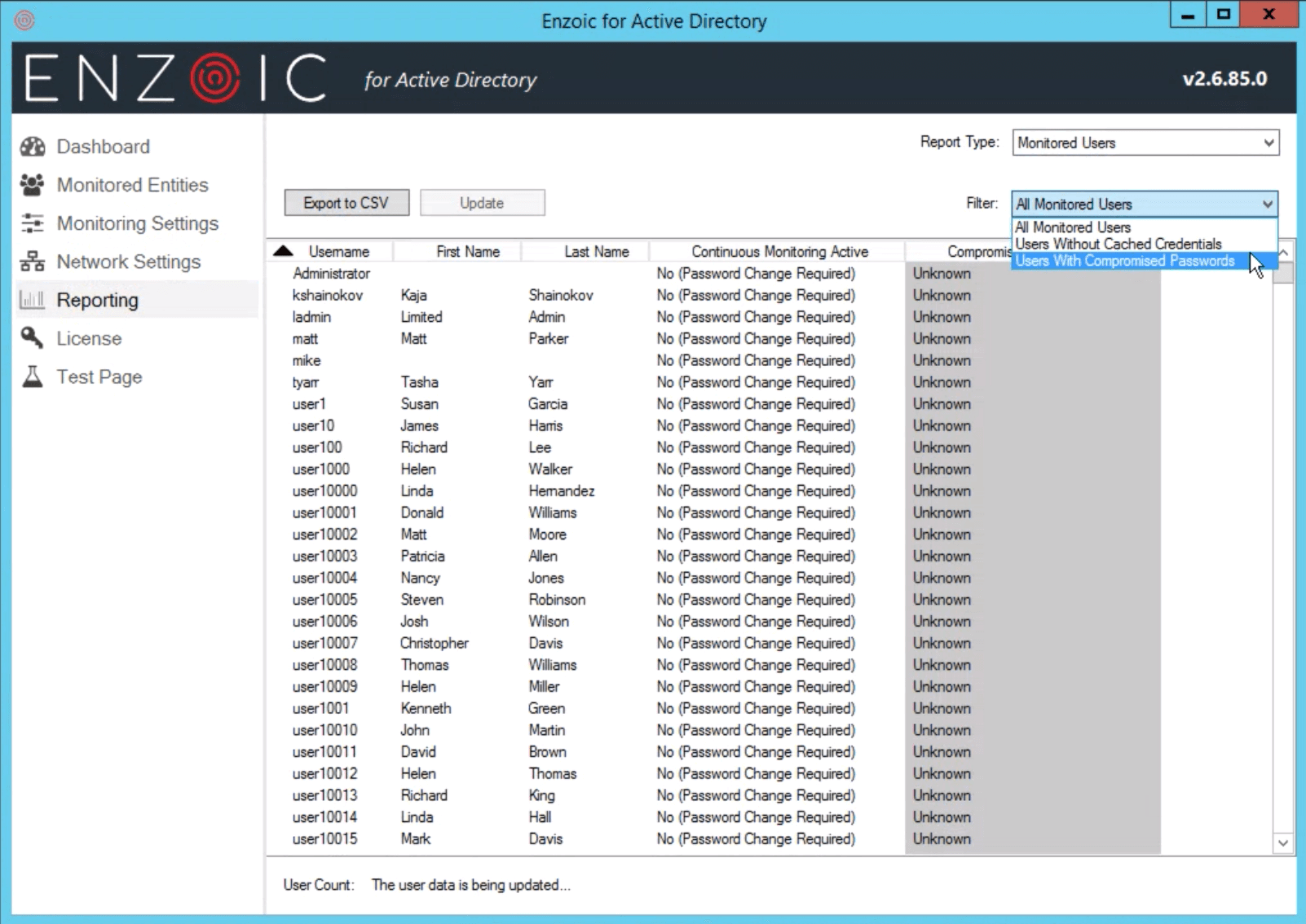
A widget on the dashboard displays the usernames of the first few compromised users (if any) and a link to the Users Report if there are too many to display. The widget is red if any user is compromised, otherwise, it is green.
A report displaying the status of all protected user accounts. Compromised accounts are clearly indicated. If an account is not being monitored, the reason is shown.
Wizard Messaging to Recommend Global Password Reset
After the initial setup is complete, a message is displayed indicating that a global password reset needs to be performed. This is necessary to initiate continuous password monitoring.
Ignore Domain Trust Accounts in User Count
Defect fixed where Trust Accounts were being counted as users.
Clean Up Server Containers on Uninstall
Defect fixed where domain controller specific data used by Enzoic was being orphaned in Active Directory.
Remove Servers from Delegate Dropdown
Remove servers from Delegate dropdown if they haven’t been seen for > 24 hours. Enzoic for Active Directory now prevents selecting a server which may be offline as the Delegate Server. A Delegate Server is the domain controller in your environment you have chosen to perform the work of Continuous Password Protection. Previously, if you selected a server that was offline or unresponsive, you would not know that Continuous Password Protection was not running.
Delete Orphan Containers on Install/Upgrade
When installing Enzoic (either upgrade or re-install), we now find and remove any orphaned application data used by Enzoic previously. An example of this would be server specific settings for a DC which has since been removed.
Start for free. Enzoic provides a clean user interface to screen for compromised passwords.
Experience Enzoic