Osterman Research Exposes the Growing Risk
The new Osterman Research report, Safeguarding Identity Security: We Need to Talk About MFA, surveyed 126 identity, IAM, and cybersecurity leaders from U.S. companies averaging 3,400 employees. The data shows a gap in security that attackers are actively exploiting:
These numbers tell us one thing loud and clear: stolen credentials are an easy doorway into an organization’s systems, and standard password policies aren’t keeping attackers out.
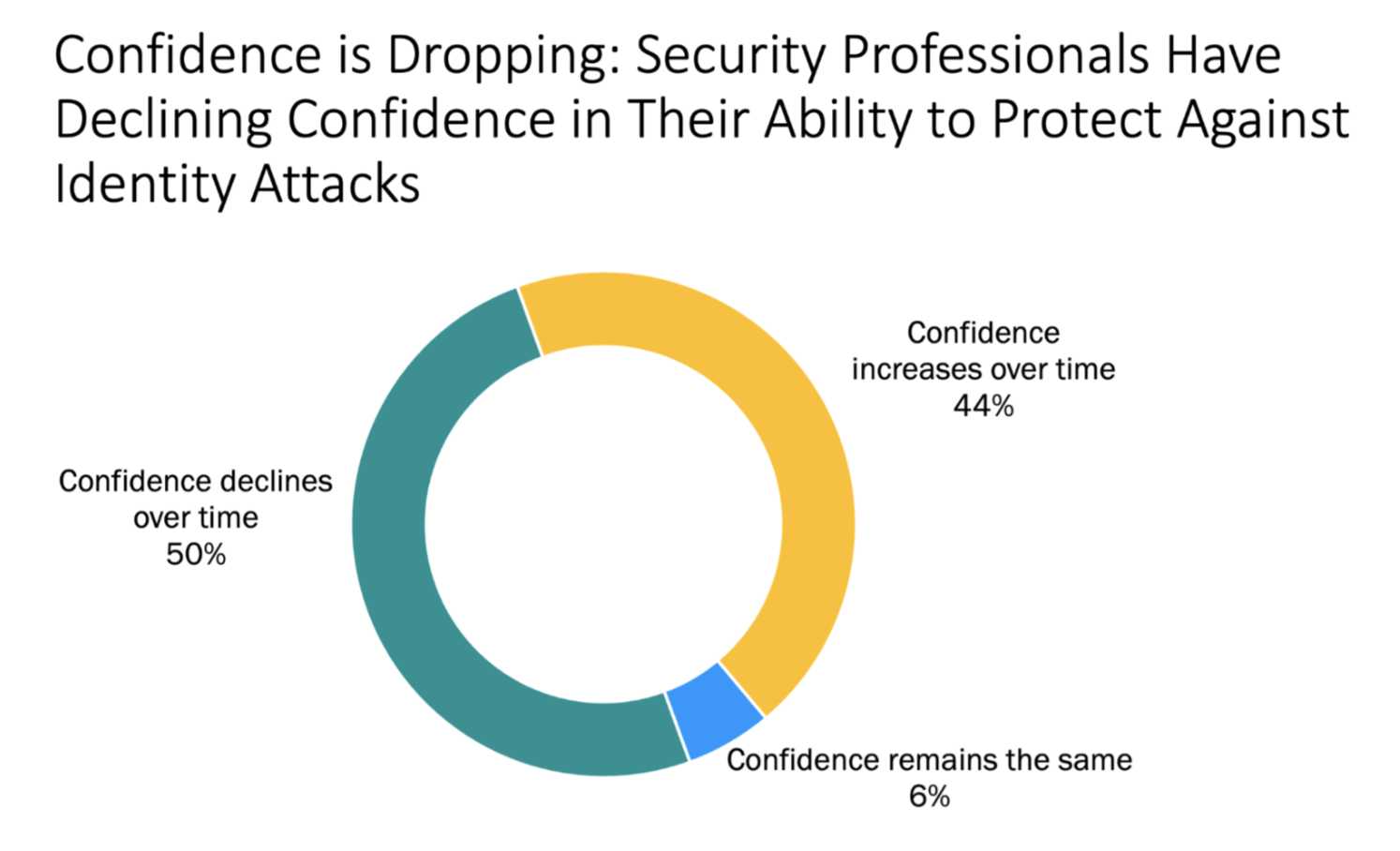
Confidence is declining: 50% of security professionals report a drop in confidence in their ability to protect against identity attacks, with compromised credentials a key contributor.
Cybercriminals know many people reuse passwords across multiple sites. So, if they get a single password, perhaps from a social media breach, they can use it to try logging into business applications. This tactic cybercriminals use is known as “credential stuffing,” where they systematically test large sets of stolen username-password combinations against different online services. Because so many people reuse their passwords across personal and corporate accounts, this technique exploits a single leaked password, like one from a social media platform, to potentially unlock other accounts.
It’s a volume game: automated tools can perform thousands of login attempts in minutes, making credential stuffing not only efficient but also alarmingly effective against organizations that aren’t actively checking for and remediating instances of compromised passwords in their environments. Even if users modify their passwords slightly (such as adding numbers, symbols, or other predictable variations) attackers can analyze these patterns, build a profile of how an individual creates passwords, and systematically test likely variations until they find a successful match. This means that even changes or additions to a compromised password provide little real protection against credential stuffing attacks.
Meanwhile, traditional password policies, like forcing regular resets and setting strict complexity rules, can backfire. Users often cope by recycling old passwords or writing them down, which can weaken security. These outdated password policies don’t match the ever-increasing risk level.
The longer compromised credentials remain undetected, the greater the risk. As Michael Sampson, Principal Analyst at Osterman Research, explains:
The longer that they (threat actors) have access to compromised credentials before they are remediated, the happier threat actors are at their ability to surreptitiously get into your environment, get access to data and applications they shouldn’t have access to, move laterally, plant ransomware, and do a whole lot of pernicious things in order to reap a financial reward as a result of that compromised credential.
– Michael Sampson, Principal Analyst at Osterman Research
The findings from the research on compromised credentials in the report are precisely what Enzoic was created to help organizations with. Here’s how:
The survey shows confidence in stopping real-time identity attacks is dropping. Organizations feel they’re on the defensive, and stolen credentials are a massive part of the problem. It’s no longer enough to rely on outdated rules; attackers have stepped up their game, and so should we.
Enzoic addresses these concerns directly. It reduces risk by reducing risk and preventing the most common attack method: the exploitation of compromised or reused passwords. It achieves this without adding friction for legitimate users.
“79% of the organizations we surveyed for this research have been compromised by one or more types of identity attacks in the past 12 months, and 86% say that cybercriminals are increasingly interested in stealing and abusing compromised credentials.”
– Osterman Research
Don’t wait for the next breach to strike. Take action now to secure your users, reduce administrative costs, and align with today’s leading cybersecurity standards.