Authentication is a cornerstone of cybersecurity, but strategies to reduce the common pitfalls and resulting security risks haven’t evolved.
In 2023, the stakes are higher than ever in the digital world, and the importance of strong authentication security cannot be overstated. Yet, despite the growing sophistication of cyber threats and the expansion of the attack surface, organizations haven’t taken action when it comes to modernizing their authentication strategies.
We recently conducted a study about ‘The State of Authentication Security’ in which 483 cybersecurity professionals, across industry sectors, to reveal the state of authentication security, and understand how credential security is prioritized—or, forgotten about.
‘Passwordless authentication’ has been shown to be somewhat of a mirage but it’s a very understandably desirable outcome given the problems faced by organizations worldwide. The password crisis is real; compromised credentials are the culprit behind more than 50% of data breaches, according to the Verizon DBIR.
However, our recent study demonstrated a mere 12% of organizations are adopting passwordless authentication, while a whopping 68% still primarily rely on traditional usernames and passwords for their authentication needs.
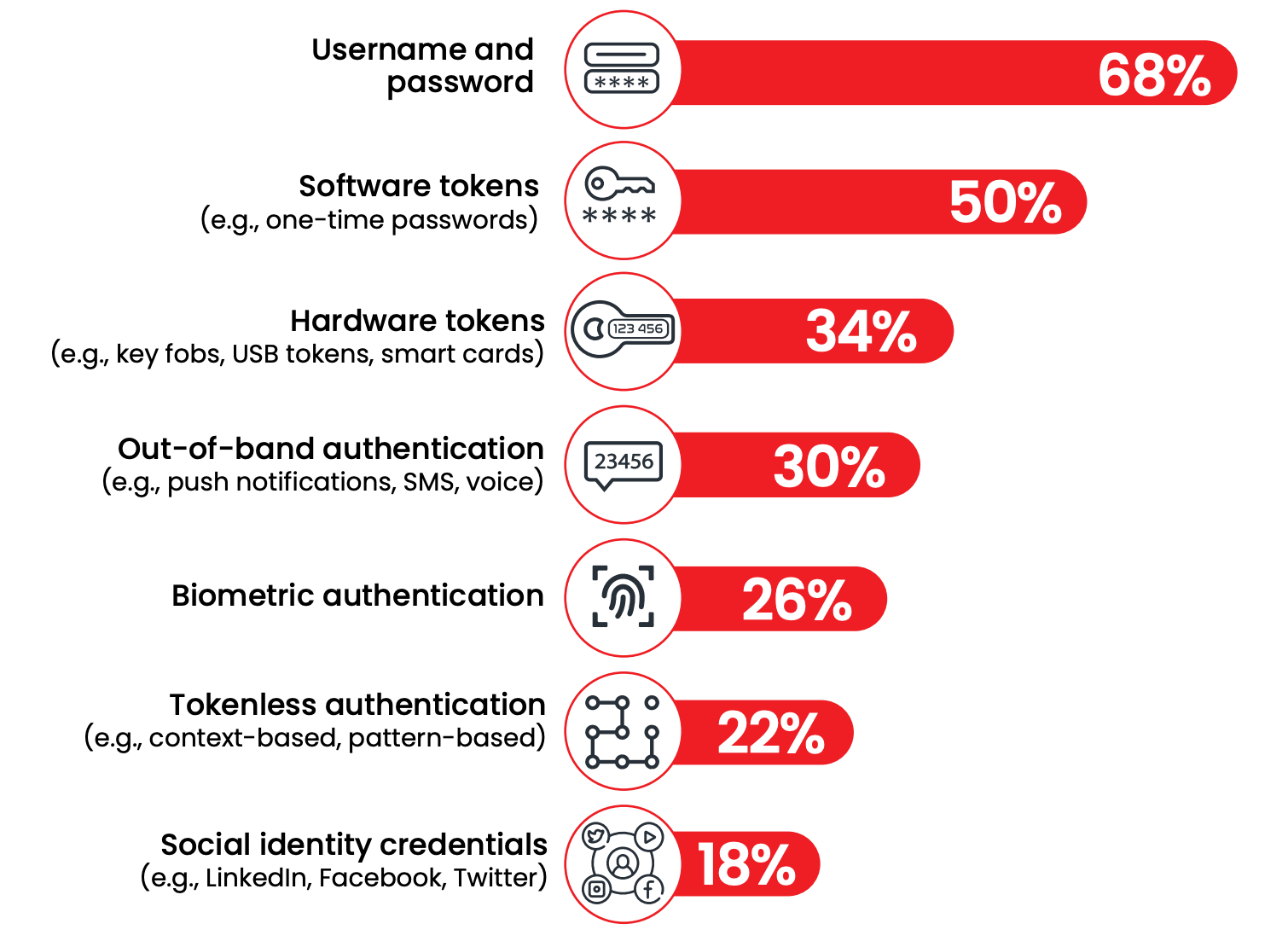
Organizations are hesitant to let go of traditional approaches, despite the hype around passwordless ideas, and the emergence of more advanced (‘passwordless’) methods like biometrics. 46% of respondents are ‘looking to phase out passwords in the next three years,’
But another 19% have no plans to do so, reflecting that despite problems, passwords remain an important authentication mechanism. This reluctance to evolve is leaving enterprises exposed to threats, as many users’ credentials are for free or for sale on the Dark Web already from previous breaches. Due to rampant password reuse, credentials become useful for threat actors looking to exploit organizations’ vulnerabilities.
While a staggering 84% of respondents in Enzoic’s survey expressed concerns about weak and compromised passwords, there seems to be a knowledge gap regarding the true extent of the threat.
Shockingly, 46% believe that only 1/5 of their passwords might be found on the Dark Web, while another 26% remain uncertain. This disconnect between awareness and reality highlights the urgent need for a reevaluation of the state of password security, and the urgent need for solutions that allow users to stay safe while using passwords.
Organizations need to take a rain check on the hope around passwordless authentication and instead take concrete steps to shore up their credential security.
Another reason organizations need to focus on password security is that the majority of those professionals surveyed continue to follow legacy practices that have actually been found to weaken credential security.
For example, 74% of companies require forced password reset every 90 days or less. Not only has this policy been shown to generate more work for employees and IT Help Desk employees alike, but it also fails to align with NIST’s most recent password policy recommendations. NIST, along with other leading organizations, had discovered employees typically select easy-to-remember passwords or swap out a single letter or character when faced with frequent resets—resulting in a weak password that threat actors can easily exploit.
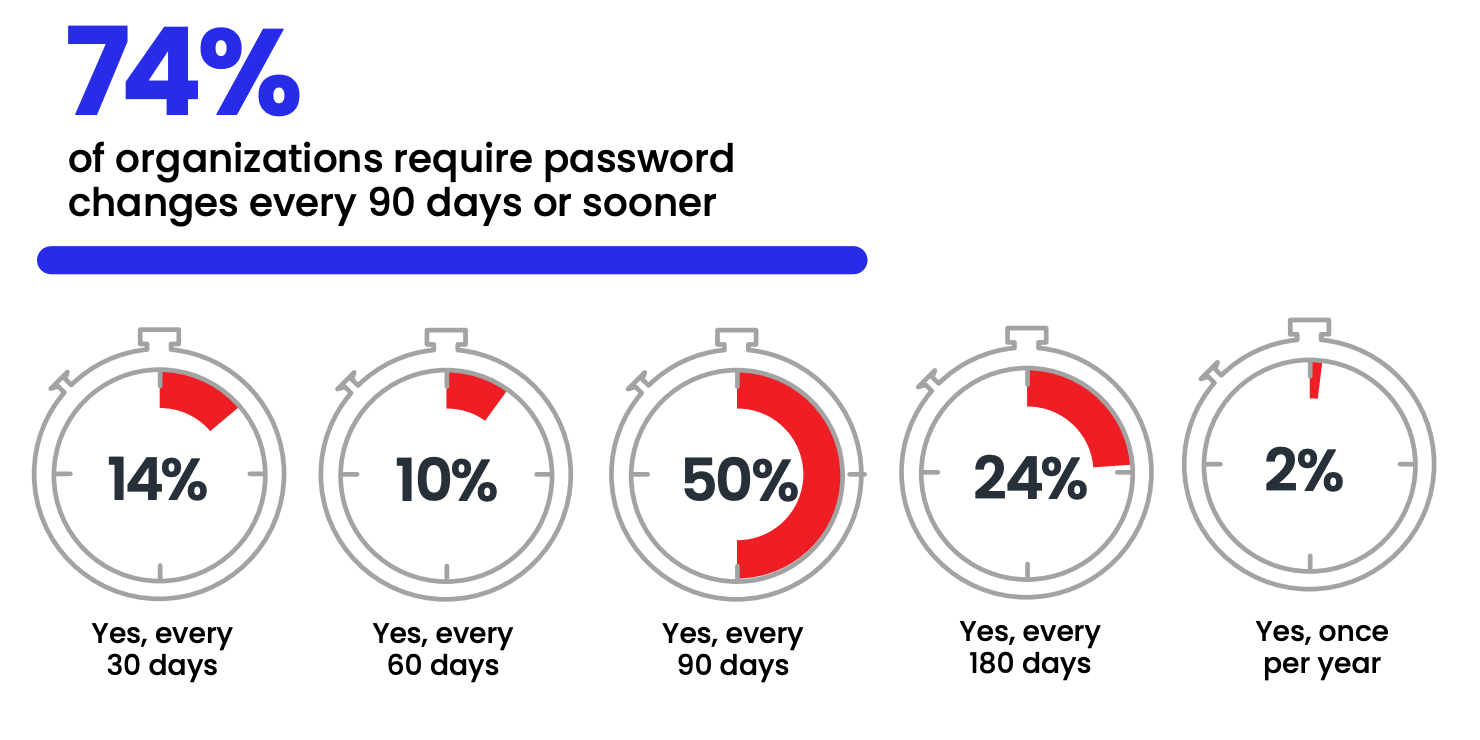
NIST password standards have been regularly published since 2017, but over half (54%) of the organizations we surveyed only learned about the framework in the last year, and a staggering 33% still hadn’t encountered the guidelines. So it’s no wonder password strategies at most companies have remained outdated.
When a business experiences a cyberattack, it’s often the moment when businesses take actions they should have taken as preventative measures. Following an attack, organizations:
However, perhaps the most surprising statistic was that 10% of organizations make no changes after an attack occurs.
Make no mistake: cyber attacks can close businesses.
Whether through a ransomware payout or the damage to the reputation, organizations need to take the impact of cyber attacks seriously.
The findings from our study underscore the urgency of managing and securing credentials, specifically passwords. The responsibility to protect organizational data rests in the business owner’s lap. It’s essential to take immediate steps to modernize your authentication security, and reduce the risk of attacks and breaches driven by compromised credentials.
Delve deeper into the findings from the State of Authentication Security Report here.
Explore free for up to 20 users. Save hours of admin time and simply get started with a password monitoring solution.