Offer actionable threat intelligence to mitigate risks associated with compromised credentials.
Contact UsGet this feature up and running in days.
Just $0.005 at each login.
Your competitors are already adopting this feature. Ensure you don’t lose market share or revenue.
OVERVIEW
Enhance product differentiation with an innovative, high-value feature that encourages action and generate additional revenue from premium customers with minimal development effort.
Enzoic Credentials SDK checks for full credentials, which is the username with the password, for compromise at every login and password change.
HOW IT WORKS
When an end user attempts to authenticate through the IAM platform, their credentials (username and password) are securely sent to Enzoic for verification. Enzoic checks these credentials against its database of compromised credentials. If the credentials are safe, authentication proceeds as normal. However, if Enzoic finds that the credentials have been compromised, it notifies the IAM platform. The IAM platform can then deny authentication and inform the user of the compromise, prompting them to reset their password. Many of your IAM competitors are already implementing this feature, so it’s essential to include it to keep your product competitive.
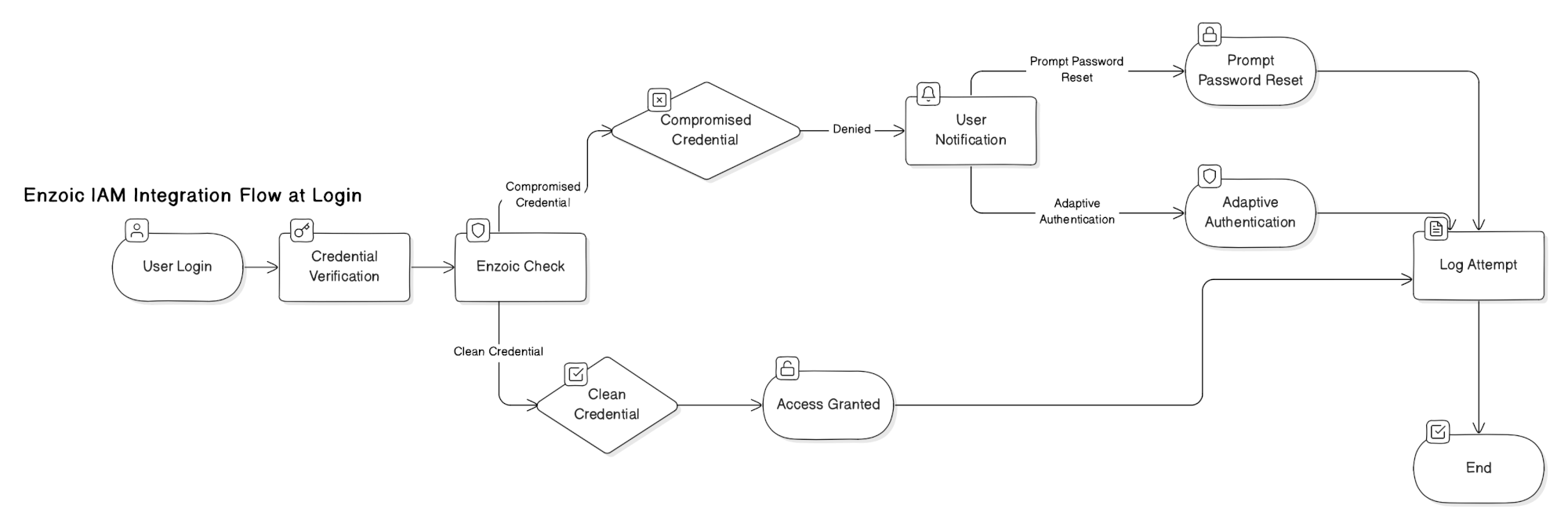
USE CASE
Proactively prevent the use of compromised credentials. The integration leverages Enzoic’s robust database of credentials compromised in data breaches, the dark web, and other sources, enabling real-time password verification.
The process initiates when an end user logs into a corporate application via the IAM platform, which sends the credentials to Enzoic for verification. Based on Enzoic’s response—clean or compromised—the platform either authenticates the user or denies access and prompts for a password reset. In scenarios such as new account setups or password resets, Enzoic detects compromised credentials, prompting the user to select a secure alternative.
The integration ensures all authentication activities are logged for compliance, operates under secure API communications, and assumes end users are educated about the importance of strong password hygiene. This setup enhances the IAM platform’s capability to mitigate risks associated with credential compromise, aligning with advanced security protocols.
Sample of how it works: https://demo.enzoic.com/
Blog
Identity and Access Management has a Password Problem. Read the blog and full report from EMA: Contextual Awareness: Advancing IAM to the Next Level.
Blog
Multi-factor authentication (MFA) is useful, but not a failsafe strategy for user authentication. Read to learn more.
Blog
The Google Threat Horizons report found that cloud computing services are facing increasing threats of compromise and abuse.
Give your customers additional security without impacting user experience.
Contact Us