The recent report on The State Password Security in the Enterprise reveals several essential findings for system administrators and security professionals alike. First, whether we are happy about it or not, passwords are going to be around for a long time. Second, organizations need to familiarize themselves with current industry recommendations. And third, due to the frequency of cyber-attacks involving compromised credentials, organizations need to jump on these authentication security concerns now.
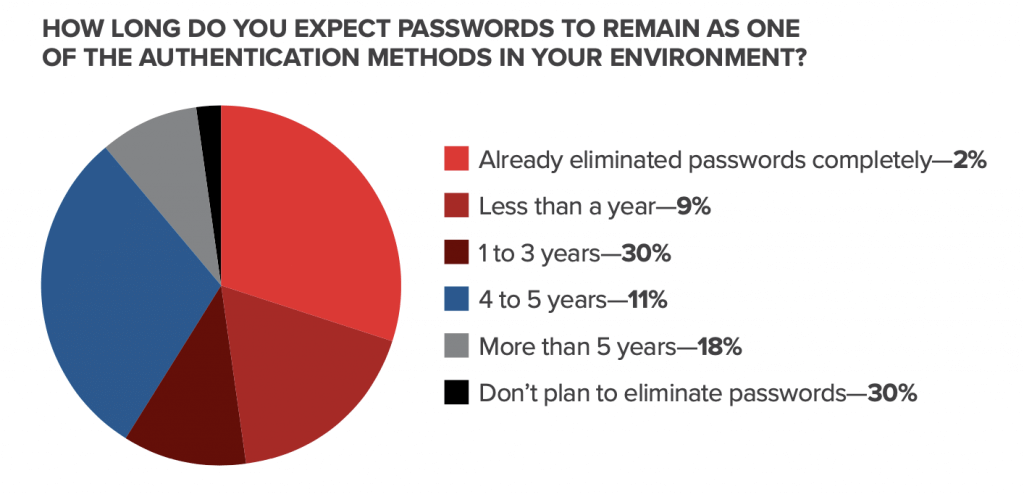
The survey found that nearly 90% of organizations “plan to continue using passwords for at least a year or more.” This comes as no surprise. Passwords, despite their controversy, are currently ingrained into most system access in some way. The survey also found that just under half (48%) of the organizations surveyed had no plans to move away from password use in the next five years, if ever.
One of the undercurrents of controversy in the password hygiene dialogue is the changing recommendations around password expiration. The National Institute of Standards and Technology (NIST) and other guiding resources advise against password expiration policies. However, some organizations are bound by conflicting compliance requirements. As a result, it’s not surprising that 47% of organizations have no plans for changes to their expiration policies. The other 53% of respondents did plan to either eliminate or “substantially extend” their policies. This divide is a prime example of how the ever-evolving best practices might take years to drive changes in habits, even when the need for change is urgent.
Dissemination of information is also a factor. According to the survey, 58% of the organizations were unaware that the NIST recommendations around password complexity had shifted. This is even though NIST formalized the changed recommendations in 2017. For example, guidelines now require screening users’ passwords against a blacklist.
When asked about cyberattack vectors they were most concerned about, 82% of respondents mentioned phishing attacks, while 53% highlighted weak/compromised passwords as their top concern. These top two concerns identified in the survey—phishing and compromised passwords—stand out because they revolve around human error. Users frequently fall for email-based phishing, leading to malware attacks, and many millions of users are currently using compromised passwords available for sale on the dark web. For illustration, a single employee’s compromised password caused one of the most recent and massive ransomware attacks.
Even when best practices are understood, implementing recommendations can be a challenge. While 53% of the organizations surveyed had compromised passwords on their minds as a threat vector, only 38% of them said they had “a method to determine when existing passwords have been compromised.” The survey also showed, 60% of the organizations have no means of determining this information now. Fortunately, there are tools available to integrate with Active Directory to make the process user-friendly and unobtrusive.
Password security is a necessity based on the statistics in the report. And until passwords are no longer in use, organizations should start reconciling themselves to the present threats and taking steps to secure their future.